
Uncompromising protection against threats
Privacy and Security
by Design
Symphony CloudSecurity is first and foremost a matter of trust. At Commend, cybersecurity as a core competency has always had a very high priority. From the initial product idea to implementation and operational support, privacy and security by design (PSBD) is the uncompromising goal and promise to our customers against which product features and functions must be measured.


Server location of Symphony Cloud is in the European Union and all personal data of our Cloud Services will be processed exclusively within the European Union.
Data Security
Commend systems use industry standard encryption of voice, video and data protects against illegal access. Commend has also implemented an ISO/IEC 27001:2013 compliant Information Security Management System (ISMS) to keep all corporate data as well as customer and supplier information safe.
- Encrypted and authenticated communication
- SIP over TLS v1.2 with secure cipher suites (> 128 bit)
- SRTP for tap-proof encrycption of voice data
- X.509 client certificates for authentification and encryption
- TLS transport encryption for the protocols HTTPS, SIPS and MQTTS to protect the web interface, APIs and video
Fail Safety – What happens if ...?
In the event of a temporary cloud connection failure, the Intercom stations use the mode Symphony Mesh to establish peer-to-peer calls. Apart from of course cloud services such as Mobile and Web Client, communication between the Intercom stations remains up and running.
Learn how we are ensuring high availability of Symphony Cloud Services.
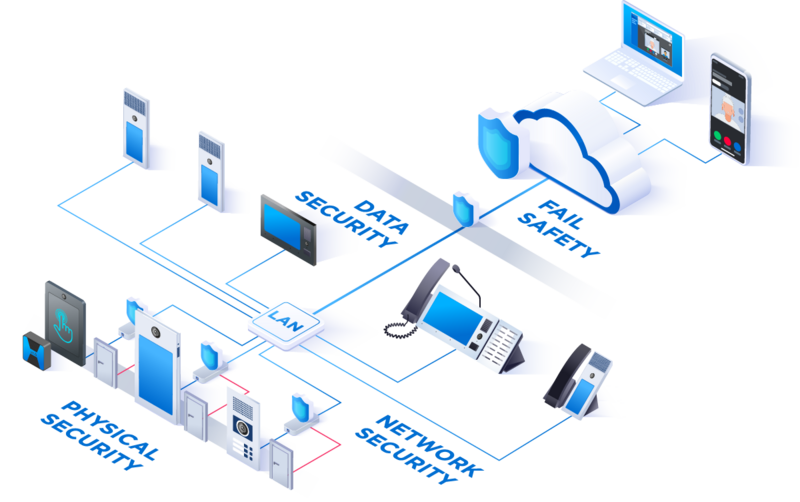
Physical Security
Symphony’s physical devices – specifically, its door Intercom stations – are, of course, the most visible attack vector in need of security hardening. Here several defence mechanisms come into play, including:
- Robust devices and vandal-resistant product versions with high IK and IP ratings
- Tamper detection through electromechanical contacts to respond to manipulation attempts
- USB and port-debugging protection
- Protection of the door opener and the IP network with the IP-Secure Connector
Threat Modelling
Cyberattacks come in an amazing variety of strategy and level of sophistication. To meet this challenge, Symphony security development is based on the STRIDE approach. This allows the developers to study potential vulnerabilities and simulate various attack scenarios (e.g., client/server spoofing, denial of service (DoS) attacks, elevation of privilege via code injection, etc.). Based on the results, they can then implement countermeasures with respect to specific security goals.
Network Security
- Standard IEEE 802.1x for authentification (network access)
- Standard IEEE 802.1q for VLANs (network segmentation)
- Commend IP Secure Connector for automatic interruption of the network connection in the event of a tampering attempt
Application Security
- Mandatory change of the default password during the first login
- Minimum password length: 12 characters
- Detection of brute-force attacks at login
- Documentation and securing of network ports