More than just a catchphrase
Privacy and Security by Design
How Does ‘Privacy and Security by Design’ Work?
The basic principle is easy: providing the best possible protection of both transferred data (e.g., audio/video streams) and ‘stationary’ data (e.g., stored user or system data) against unauthorised access in order to ensure the availability of products and services.
The methods used to achieve this range from latest-generation cryptography
to secure standard Internet protocols and a comprehensive defense-in-depth strategy.
Commend products are always designed, developed and incorporated in customer solutions in accordance with these security criteria. System functions integrate natively and seamlessly with the built-in security components. This lets Commend solutions stand out against other systems that apply add-on security components retroactively.

Partnerships and Best-practice Standards
Commend's dedication to Cyber Security is exemplified through its strategic partnership with SBA Research, focusing on the principle of "Privacy and Security by Design" for our cloud-native "Symphony" products. By collaborating with the Vienna-based IT Research think tank, we have completed a vital project phase that enhances our Dev-Sec-Ops development process with a proactive security posture.
A pivotal aspect of this new strategy is the 'shift-left approach'. It brings security testing forward in the development process, integrating it into the earliest stages of product design and coding. Rather than waiting until a product is fully developed, Commend's engineers, with insights from SBA Research, systematically analyze and test for security vulnerabilities from the get-go. This enables the detection and mitigation of potential risks much earlier, which is more effective and less costly than addressing them later in the process. It's a significant shift from traditional development practices, where security checks were later in the process or even performed only after the main build is completed.

By using advanced research methodologies like mathematical modeling and security testing from the MATRIS Research Group, Commend's engineers can evaluate security aspects during the design phase, even before coding begins. This ensures that each line of code contributes to the overall security of the product. The results have been impressive, with the Symphony platform demonstrating strong resilience against intensive penetration tests, reflecting the robustness of its “privacy and security by design” principle.
Commend's shift-left strategy, supported by cutting-edge research and a thorough quality assurance framework, signifies a substantial leap towards achieving the highest possible level of Cyber Security for our clients. This systematic integration of security at every stage of product development again sets a high standard for the industry and provides our customers with the assurance of a highly secure IT infrastructure.

Partnerships and Best-practice Standards
To keep up with the fast-paced technical developments with respect to ‘Security by Design’, Commend maintains research and development partnerships with third-party manufacturers, security experts and universities while leveraging its membership in security-specific organisations such as the Center for Internet Security (CIS).
Cyber-secure on multiple levels
With cyber-crime on the rise, system hardening and the protection of on-premise Commend solutions and cloud-native Commend Symphony services against security breaches is at the forefront of our product development process. In final installations at the customer's site our “Privacy and Security by Design” approach extends to a combination of measures in four basic layers:
Physical Security – this provides physical protection to security sensitive components such as networked door call terminals and the like. Measures employed for this purpose include Commend IP Secure Connectors that cut the network connection in case of device tampering to fight off hacking attempts.
Network Security – this ensures secure network connections of on-premises components, as well as web-based and Symphony cloud-native services.
Security-controlled access to network infrastructures goes hand in hand with Data Security measures (such as point-to-point encryption) in accordance with proven norms and standards. It is precisely for this reason that the cloud native Commend Symphony platform has been developed from the start to be “secure by design” in line with Commend's holistic Privacy and Security by Design (PSBD) approach. In keeping with this commitment, Commend has also implemented an ISO/IEC 27001:2013 compliant Information Security Management System (ISMS) to keep all corporate data as well as customer and supplier information safe.
Fail Safety – various measures, from automated updates to cloud-native failover strategies are used to ensure uninterrupted availability of Commend systems and services, even in case of a network connection failure.
As a result, multi-level cyber security allows users to enjoy Commend service performance on the highest level.
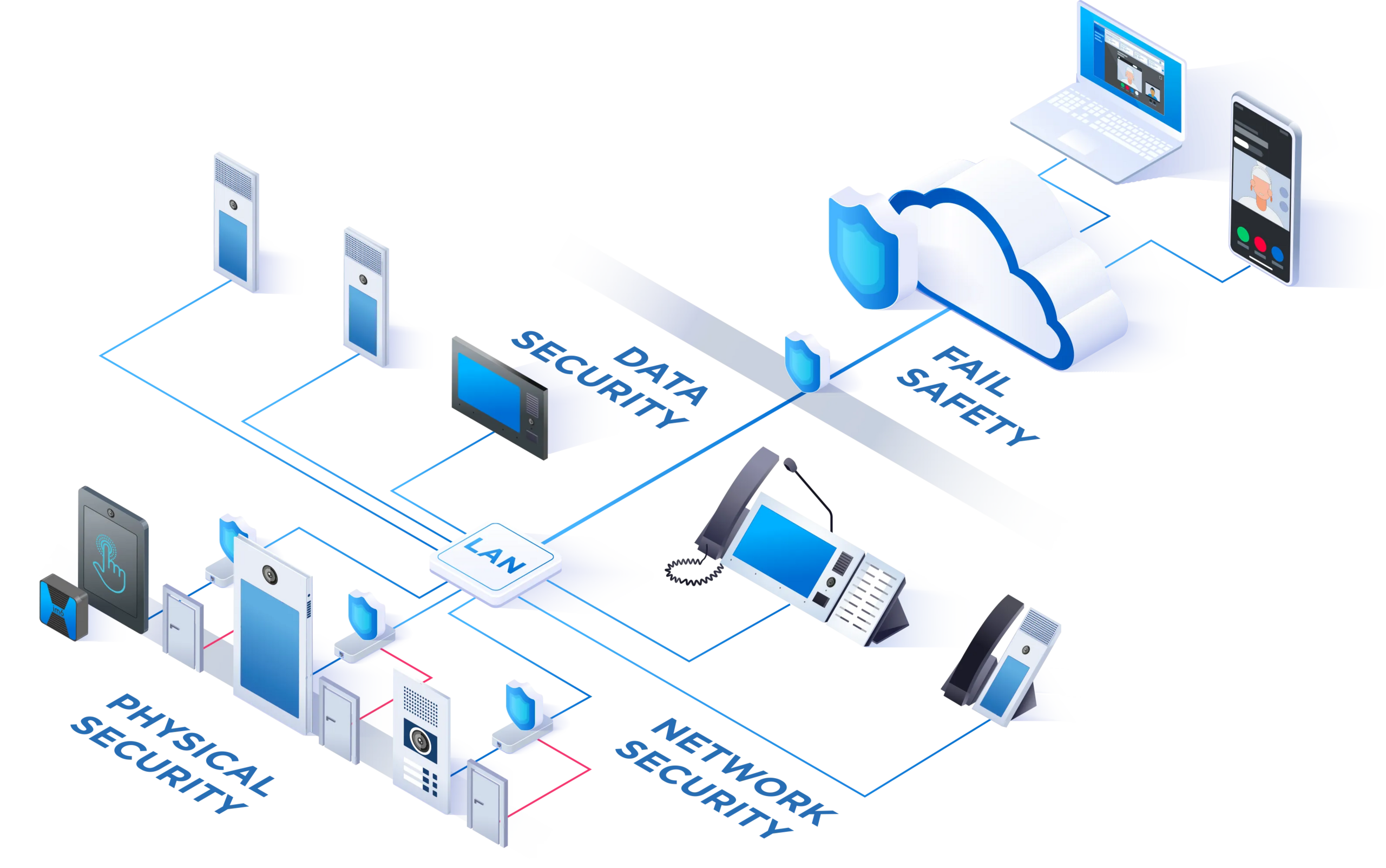
Physical Security
- Robust Intercom stations
- Vandalism protection/impact resistance
- Tamper detection
- Protection of the door opener
Network Security
The IP-Secure Connector mounted in a protected indoor area, shields especially the IP-Network and also the door opener from the outside.
Data Security
Industry standard encryption of voice, video and data protects against illegal access.
Fail Safety
Even if the Internet connection fails, operation within the network is assured. This is made possible by the distributed server intelligence in the intercom stations.