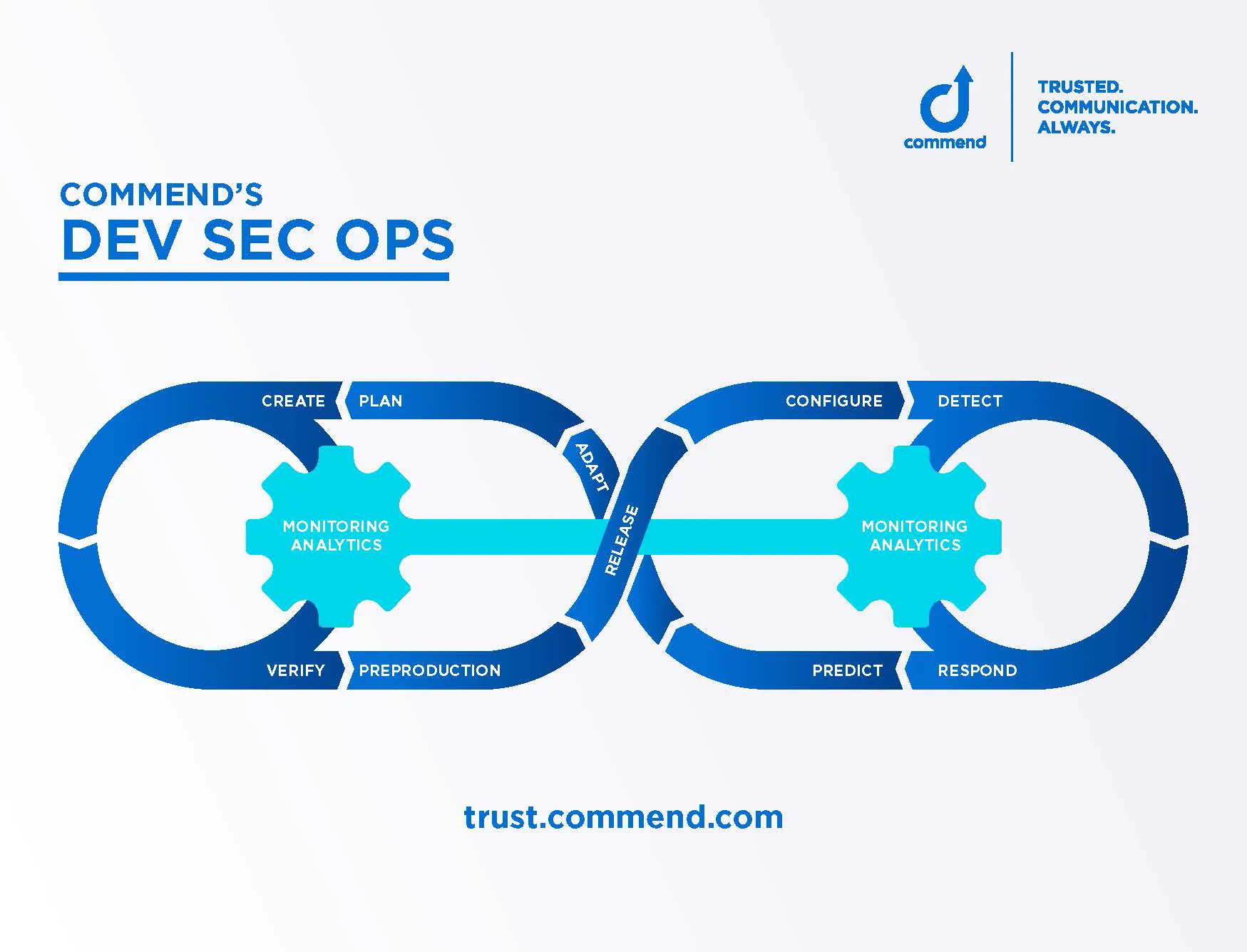
At Commend we design and operate our Symphony services – like the Symphony Door Call solution – from the ground up on the principle of ‘Security by Design’. As a central element of our defence in-depth strategy, cyber security is firmly embedded in all our developments. We are living up to this promise by having our processes certified regularly by independent auditors in accordance with stringent norms and standards. IEC 62443 for example, the international security standard for product development lifecycle requirements.
How does all this work in practice? Let’s take a look behind the scenes at our Symphony development labs.